Functionality
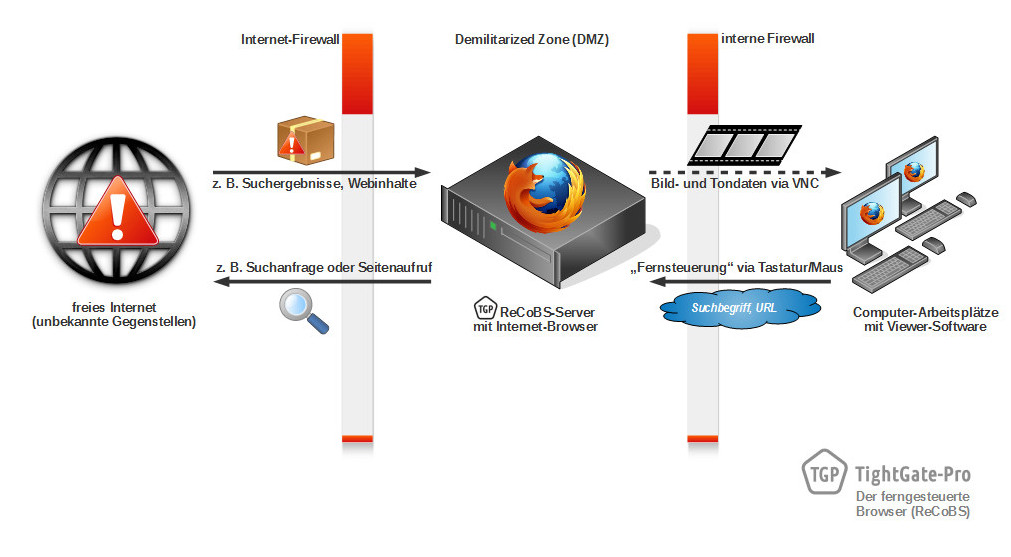
TightGate-Pro is based on the so-called ReCoBS method. ReCoBS stands for Remote-Controlled Browser System and refers to a "remote-controlled web browser". The execution environment of the web browser is physically separated from the workstation computer. In this way, the system helps to effectively shield the internal network from the Internet. TightGate-Pro thus protects against attacks from the Internet that exploit security vulnerabilities in widely used web browsers.
During operation, the web browser is no longer executed locally on the workstation computer, but within a secure execution environment. The workstation computer only receives the browser's screen display in the form of graphics. Mouse and keyboard inputs are transmitted in reverse from the workstation to the remote control of the browser.
There are hardly any changes to day-to-day work. Instead of the local web browser, you start TightGate-Pro via the start menu or a desktop icon.
Hinweis
While using the Internet via TightGate-Pro is largely the same as using a local web browser, the procedure for downloading files from the Internet is different. In this context, please pay particular attention to the Notes in this user manual and follow the instructions of your system administrator.